HackerOne’s Pentest as a Service Enhancements Streamline Secure Testing for Large Enterprises and Digital Innovators ejames@hackerone.com
Other content in this Stream
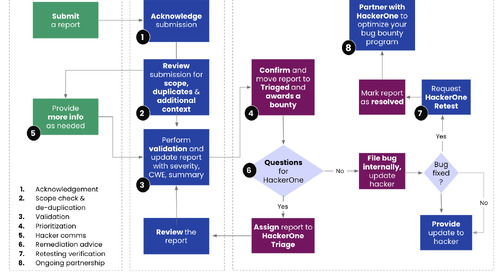
Like triaging in a hospital emergency room, security issues must be diagnosed and handled by an expert as soon as they arrive. But it doesn’t stop there. Just as an ER needs good doctors, a triage...
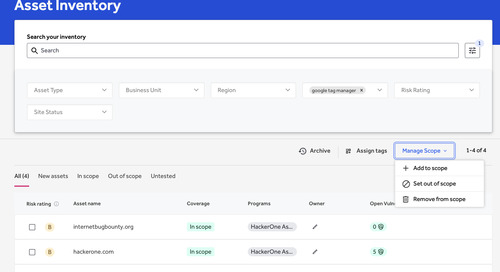
This blog post is part 1 of an ongoing series that provide deep dives into HackerOne Assets and its core capabilities. Having the right automated tools to monitor your known attack surface is...

So, who is Corb3nik? My name is Ian, also known as Corb3nik on social media. I’m a long time CTF enthusiast and bug bounty hunter. Currently, I’m the co-founder for a web security toolkit called...

So, who is Corb3nik? My name is Ian, also known as Corb3nik on social media. I’m a long time CTF enthusiast and bug bounty hunter. Currently, I’m the co-founder for a web security toolkit called...
Newly Introduced HackerOne Assets Goes Beyond Attack Surface Management To Close Security Gaps alice@hackerone.com Thu, 10/13/2022 - 01:56 Read more about Newly Introduced HackerOne Assets...

When I joined HackerOne last year, the vitality of the hacker community drew me to this organization. And as Chief Hacking Officer, I see the impact this community makes daily. Together, we’ve...

In the last two years of their bug bounty program, the hacker community has helped TikTok identify and disclose 450 vulnerabilities in their public-facing assets. In response, TikTok has awarded...

October is Cybersecurity Awareness Month, but at HackerOne, we’ve decided it should be Hacker Awareness Month. We want to spend October celebrating the individuals that drive our platform —...
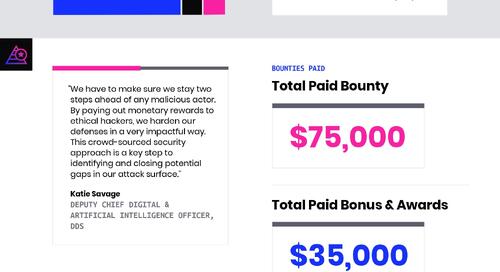
HackerOne met with Katie Savage, Deputy Chief Digital & Artificial Intelligence Officer at DDS, and Melissa Vice, Director, DoD VDP at DC3 from the organizing teams of Hack U.S. to discuss the...
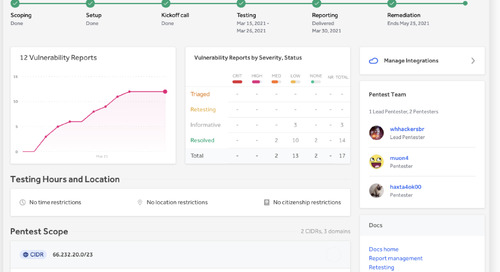
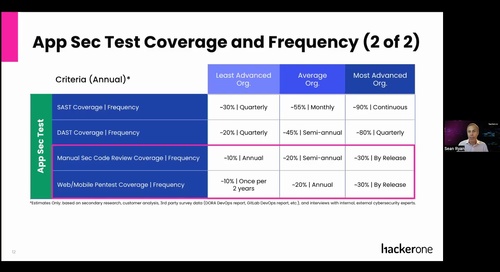
New capabilities improve pentesting to increase attack resistance The enhanced features drive robust security testing practices with the ability to launch, test, identify, retest, and fix...

Are you a veteran hacker, someone who loves code review, or looking to get your first CVE? Then, I have something to share with you. Let's talk about the Internet Bug Bounty (IBB). Wide Open...
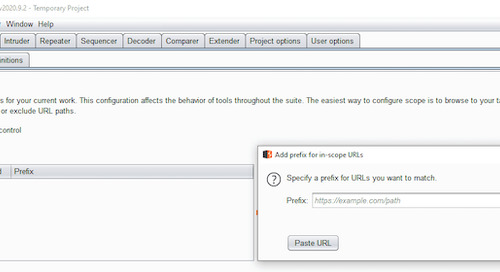
This post will start with the basics of defining scope and how ethical hackers and testers use it in their testing workflow. If you’re already familiar with Burp Suite and the general idea of...

Today's Hacker rez0 JXoaT: What was your first experience with hacking growing up? rez0: I think, at least for the word 'Hacking,' my experience comes from majoring in computer science. Like, I...

Who are you? My name is Adnan Malik. I’m a web application security researcher, penetration tester and bug hunter. I currently run a startup named “Secure Purple,” which is cyber safety and...
HackerOne Appoints Dawn Mitchell as Chief People Officer ejames@hackerone.com Thu, 08/18/2022 - 09:55 Read more about HackerOne Appoints Dawn Mitchell as Chief People Officer ...

So, who is Corb3nik?My name is Ian, also known as Corb3nik on social media. I’m a long time CTF enthusiast and bug bounty hunter. Currently, I’m the co-founder for a web security toolkit called...