Newly Introduced HackerOne Assets Goes Beyond Attack Surface Management To Close Security Gaps alice@hackerone.com
See our HackerOne Assets video & sign up for a free demo!
Get StartedOther content in this Stream
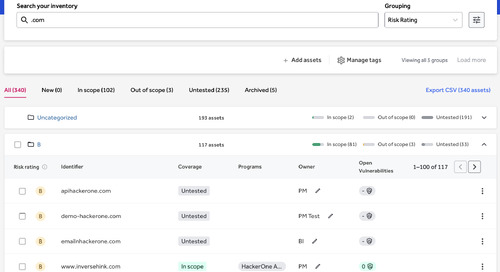
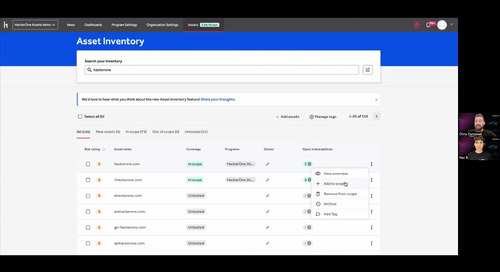
What is Asset Inventory? The effectiveness of an ASM initiative is determined by how well the solution records the attack surface and presents the data to the organization. A best-in-class ASM...

Why is ASM Important? Your attack surface is the sum of all entry points an attacker could use to access your systems, applications, devices, or network. For most organizations, it’s a complex...
We recently sat down with Wendy Ng, Principal Cloud Security Architect at OneWeb, to talk about their experience with their private HackerOne bug bounty program. Wendy shared OneWeb’s approach to...
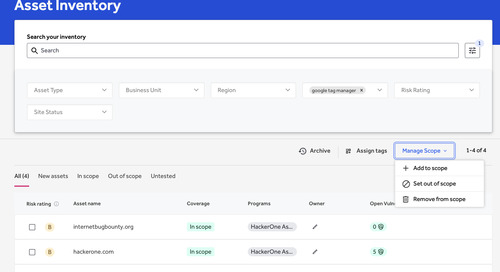
This blog post is part 1 of an ongoing series that provide deep dives into HackerOne Assets and its core capabilities. Having the right automated tools to monitor your known attack surface is...
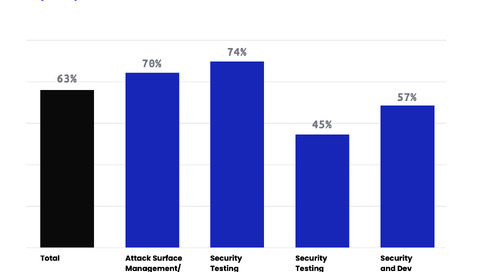
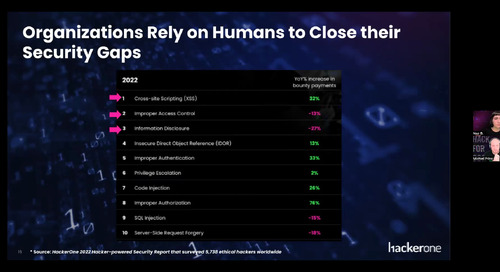
Attack Resistance Management is the management of human security tests on your attack surface designed to increase your resistance to attackers. It is a cross-functional and continuous approach to...
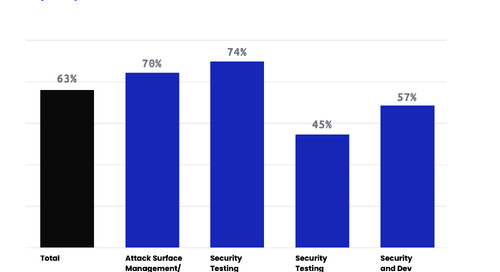
Attack Resistance Management is the management of human security tests on your attack surface designed to increase your resistance to attackers. It is a cross-functional and continuous approach to...

HackerOne's 2022 Attack Resistance Management report will help you close your security gaps by showing how to continuously improve visibility and remediation across your attack surface.
Today, HackerOne published The 2022 Attack Resistance Report: A HackerOne Security Survey. Our research revealed an increasing gap—the attack resistance gap—between what organizations can defend...

Understanding where the critical flaws lie within your organization’s attack surface is critical—but complicated.
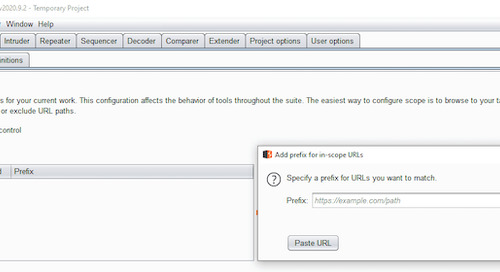
This post will start with the basics of defining scope and how ethical hackers and testers use it in their testing workflow. If you’re already familiar with Burp Suite and the general idea of...

Beiersdorf’s cybersecurity team is always thinking about the best ways to secure their public-facing assets. As their digital footprint increases, they add new processes and systems to align with...
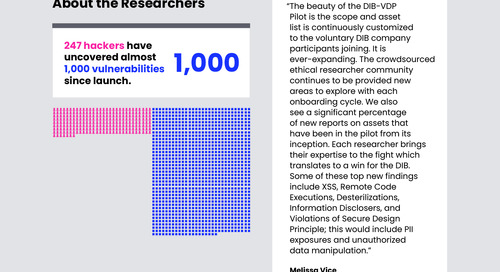
Maintaining the security of the digital assets within the Defense Industrial Base (DIB) contractor networks helps defend the United States of America. For the last nine months, Department of...

HackerOne CEO, Marten Mikos, kicked us off by talking about the last year in cybersecurity. “New and significant attacks related to high-profile supply chain vulnerabilities,...
UK Ministry of Defence Embraces Hackers to Secure Digital Assets hackerone@visi… Tue, 08/17/2021 - 09:07 Read more about UK Ministry of Defence Embraces Hackers to Secure Digital AssetsAugust 3, 2021