Learn how Zebra Technologies leveraged the HackerOne Platform to improve customer trust, gain more robust coverage for rogue digital assets, increase oversight and confidence in security, and achieve revenue growth.

Speak with a Security Expert
Other content in this Stream
Insights from our customers & the world's top hackers—emerging threats, vulnerability rankings, & fighting cybercrime on a budget
Today’s security leaders have limited resources while facing a nearly infinite number of systems, services, solutions, and threats.
Spiraling inflation and the pervading security skills gap have security leaders struggling to keep up. Our new eBook outlines strategies gathered from 50+ leaders.
Recently updated for 2023 and packed with incredible insights, the latest version of The Security Leader's Handbook is a must-have resource for cybersecurity leaders like you.
HackerOne Security Advisory Service is designed to optimize the outcomes of your continuous security strategies and ensure your security safety net is strong.
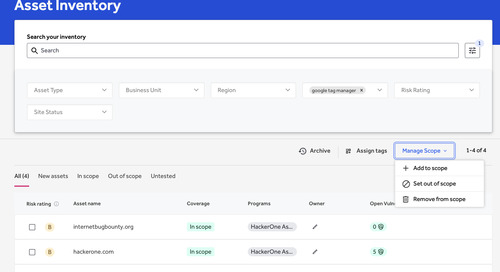
This blog post is part 1 of an ongoing series that provide deep dives into HackerOne Assets and its core capabilities. Having the right automated tools to monitor your known attack surface is...
Today, HackerOne published The 2022 Attack Resistance Report: A HackerOne Security Survey. Our research revealed an increasing gap—the attack resistance gap—between what organizations can defend...

So, who is Corb3nik? My name is Ian, also known as Corb3nik on social media. I’m a long time CTF enthusiast and bug bounty hunter. Currently, I’m the co-founder for a web security toolkit called...

So, who is Corb3nik? My name is Ian, also known as Corb3nik on social media. I’m a long time CTF enthusiast and bug bounty hunter. Currently, I’m the co-founder for a web security toolkit called...
Newly Introduced HackerOne Assets Goes Beyond Attack Surface Management To Close Security Gaps alice@hackerone.com Thu, 10/13/2022 - 01:56 Read more about Newly Introduced HackerOne Assets...

When I joined HackerOne last year, the vitality of the hacker community drew me to this organization. And as Chief Hacking Officer, I see the impact this community makes daily. Together, we’ve...
![Common Vulnerability Scoring System [CVSS] | A Complete Explanation](jpg/hac_blog_common%2520vulnerability%2520scoring%2520system-main_featured_560x494_l2r1659b.jpg?url=https%3A%2F%2Fwww.hackerone.com%2Fsites%2Fdefault%2Ffiles%2FHAC_Blog_Common%2520vulnerability%2520scoring%2520system-Main_Featured_560x494_L2R1.png&size=1&version=1690208403&sig=1fd82a9e68b87934c3b28aa3aa5ddfcb&default=hubs%2Ftilebg-blogs.jpg)
How Does CVSS Work? Vulnerabilities are flaws in an organization's internal controls, information systems, or processes that cybercriminals can exploit to steal corporate data and cause...

In the last two years of their bug bounty program, the hacker community has helped TikTok identify and disclose 450 vulnerabilities in their public-facing assets. In response, TikTok has awarded...








