What Are the Key Differences Between Bug Bounty and VDPs?
A VDP is a structured method for third parties, researchers, and ethical hackers to report vulnerabilities easily. A bug bounty is a reward that organizations offer to ethical hackers for discovering bugs.
Organizations use a VDP to establish clear guidelines for anyone who discovers vulnerabilities. These guidelines outline where to report found vulnerabilities, provide safe harbor for researchers, and present an area to submit findings.
VDP guidelines also help protect researchers from legal action while shielding organizations from public vulnerability releases. Occasionally, organizations reward researchers through a VDP but do not pay per vulnerability.
Hackers disclose vulnerabilities for both VDP and bounty programs. The key difference is that bounties pay out cash for each vulnerability discovered.
The hacker community often seeks high bounties, allowing organizations to attract top talent with greater rewards. VDPs offer a similar platform for disclosure but typically don’t attract as much attention, in large part, because they don’t pay out bounties.
VDPs allow businesses to set a wider scope with more assets researchers can test and report on whereas bounty programs usually have set targets with reward tiers and determined SLA times.
While there is some overlap between VDP and bounty programs, knowing how each one works can help you understand which is suitable for your organization.
How Does a Bug Bounty Program Work?
Each bounty program starts with a scope that defines the assets available for testing and the project’s reward budget. Scope helps organizations narrow where hackers should focus their efforts. Bounties can be public or private, allowing organizations to select which hackers can participate in their program.
When hackers participate in bug bounty programs, many earn full-time incomes. Bounties attract a diverse and talented group of hackers. Timeframes are flexible and allow companies to toggle their bounty programs on and off as they see fit.
When hackers discover a vulnerability, they fill out a disclosure report with the bug’s severity, technical details, and impact. These details help the security team validate the issue and build a patch to fix it. When the developers confirm the bug is valid, the organization pays the hacker the bounty. The bounty payout amount is dependent on the criticality, frequency, and impact of the bug.
How Does a Vulnerability Disclosure Program Work?
A VDP works by providing a platform and methodology for anyone to disclose bugs to an organization. It also lets the finder know what to expect in terms of communication and remediation. Having a VDP streamlines the remediation process. Since this can take longer for more complex vulnerabilities, a process is essential.
VDPs are public-facing, allowing anyone visibility into an organization’s active program. The program provides a straightforward method to communicate findings and to show customers and investors that the organization takes security seriously.
Established VDPs help prevent researchers from disclosing vulnerabilities publicly without the organization's knowledge first. VDPs give organizations a chance to develop a patch and disclose the issue once a solution is ready.
Similar to bug bounty programs, VDPs have a disclosure submission process. -Finders submit reports outlining how bad actors can exploit the vulnerability, which systems it impacts, and the bug’s severity. Many VDPs have time restrictions before the vulnerability goes public. For example, If an organization cannot fix a bug in 30 days, the issue will go public so users can take corrective action.
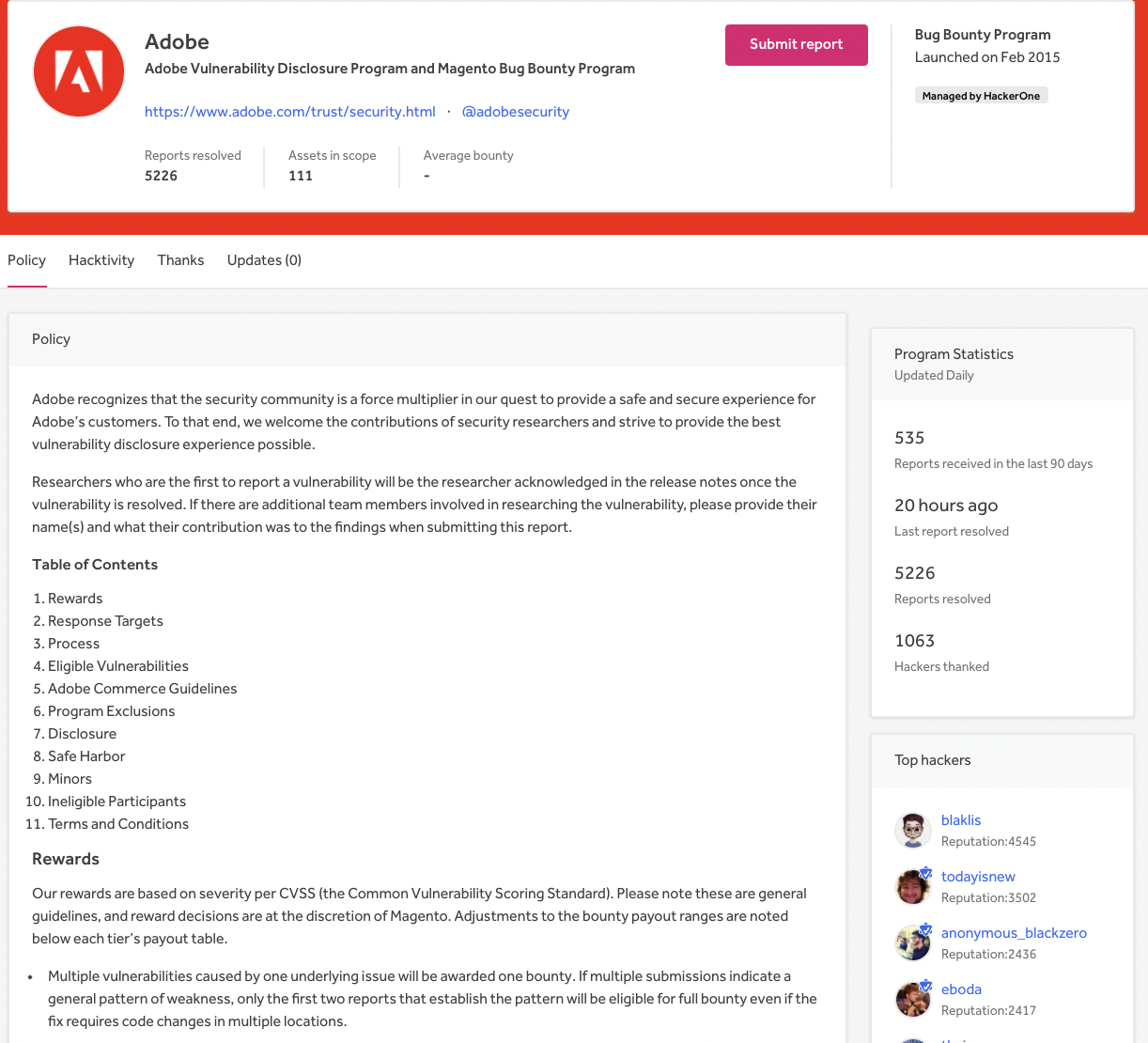
Many organizations have combined VDPs and bug bounty programs. Figure 1 below shows HackerOne customer Adobe’s Vulnerability Disclosure Program and Magento Bug Bounty Program Policy’s Table of Contents, Rewards, and Tier 1 structure.
Starting Your Bug Bounty or Vulnerability Disclosure Program with HackerOne
HackerOne Response (VDP) and HackerOne Bounty help identify vulnerabilities quickly and deliver continuous testing for both full and targeted asset coverage. Contact us today to learn more.