Bug Bounty: Outmatch Cybercriminals and Minimize Your Threat Exposure
Tap into a legion of ethical hackers to pinpoint application vulnerabilities and minimize your threat exposure around the clock.
See HackerOne Bounty in action
Preemptive security testing that scales with your business
A fully managed bug bounty program with HackerOne enhances your in-house team by leveraging a global pool of security experts to detect costly vulnerabilities without hindering innovation.
What is Bug Bounty?
A bug bounty is a monetary reward given to ethical hackers for successfully discovering and reporting a vulnerability or bug to the application's developer. Bug bounty programs allow companies to leverage the ethical hacking and security researcher community to improve their systems’ security posture over time continuously. Bug bounties can complement existing security controls by exposing vulnerabilities that automated scanners miss, and incentivize security researchers to emulate what a potential bad actor would attempt to exploit.

Skills you need, expertise you can trust
Close internal skills gaps by mapping your technology stack to varying backgrounds, skill sets, and perspectives to cover diverse attack surfaces including web, cloud, mobile, IoT, and more. Our bug bounty redefines the traditional static, signature-based model of security testing by providing an offensive perspective on the enterprise internet environment.
- Leverage HackerOne’s global community to aid in your rapid response in the event of another zero-day like log4j. Access experts in cloud, mobile, hardware, IoT and more.
- Select ID-verified and background-checked ethical hackers to analyze sensitive internal assets. Additional verification requirements provided by our Clear offering include citizenship, residency, age restrictions, and proven performance levels.
- Monitor and access control to sensitive assets using our Gateway solution, powered by Cloudflare.

Workflows that adapt to your development life cycle
With HackerOne’s DevSecOps integrations, embed real-world security feedback directly into your existing toolset to accelerate response, reduce risk, and scale your bounty program.
- Integrate vulnerability findings with the security and development tools you use today.
- Fix vulnerabilities faster with remediation guidance and retesting capabilities.
- Direct hacker attention to new product and feature releases with time-bound bounty incentives.

Triage you can count on
HackerOne Triage services remove the burden of validating incoming vulnerability submissions. Our triage team communicates with hackers, validates their submissions, removes duplicates, and ranks the remaining vulnerabilities by severity.
- Eliminate false positives, and accelerate remediation.
- Our team manages ethical hacker communication and provides you with actionable reports.
- Proven track record of speed, accuracy, and responsiveness.

Size up potential threats and take action
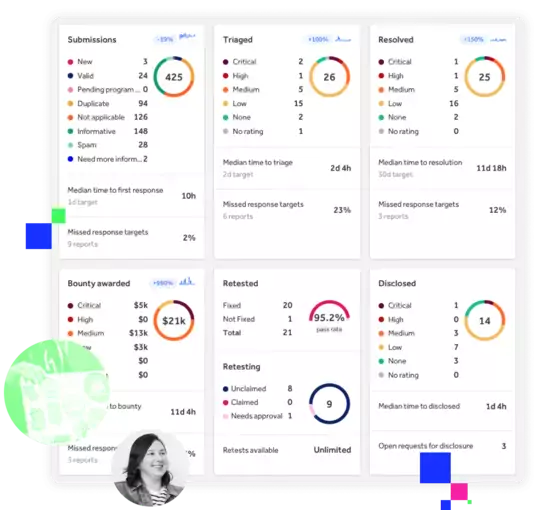
HackerOne’s centrally-managed SaaS platform tracks the health of your bug bounty program and helps prioritize which vulnerabilities pose the greatest risk to your business.
- Real-time analytics showcase key program metrics including response targets, submissions, bounty spend, remediation status and more.
- See how your high-severity issues stack up against industry norms and track effectiveness
- Access scoring data that uses Common Vulnerability Scoring System (CVSS) and Common Weakness Enumeration (CWE).




The ideal end-state is that bug bounties become a regular, common tool in securing all IT assets across the Department of Defense. We will always have security vulnerabilities. We can approach that reality one of two ways: we can deny it, or we can be proactive, open to it and use every tool in our toolbox to remediate or mitigate them.

The program has been successful because of the continued contributions from diverse, talented researchers, security engineers who triage and guide teams to remediate, and our engineering team that is always enthusiastic to learn from these bugs.

We are a trust based business to an extreme extent. One of the best ways for us to augment our internal security team is to work with the hacker community. This was a pain before HackerOne but now is significantly easier.
Want to learn more about how a bounty program can reduce risk?
Tell us about the challenges you are hoping to overcome and one of our experts will contact you.
Real-world security insights protect your business
HackerOne Bounty connects you with global security expertise with integrations into your existing workflows.

HackerOne Bug Bounty
As a key capability of the HackerOne Attack Resistance Platform, HackerOne Bug Bounty helps minimize your threat exposure by leveraging a legion of ethical hackers to provide preemptive and continuous oversight for your expanding digital landscape.

How Ethical Hackers Are Helping Security Leaders Navigate the Budget Crunch

The Executive Guide to Human Security Testing
Beginner-friendly guide showcasing how an offensive testing program can reduce risk to your organization.





