Code Security Audit
Uncover complex vulnerabilities that scanners alone can’t
HackerOne’s cutting-edge Attack Resistance Platform automation and manual review from 600+ experts proactively eliminate vulnerabilities before attackers have a chance.
Lower risk without compromising velocity
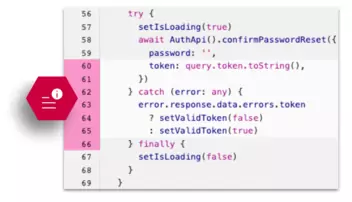
Our network of background-checked, skills-vetted engineers scour your source code for security flaws, escalating risks that need attention and providing context-specific remediation guidance—so issues can be resolved fast without slowing down progress.


This was our first time using HackerOne Code Security Audit. We didn't know what to expect, but it turned out to be everything we had hoped for. The analysts’ feedback was specific, well-documented, and security-focused. The communication between all parties was excellent and timely. The Fidlar team’s security expertise has grown during this experience with HackerOne.

Seamless integration
Connect securely to repository source code providers such as GitHub, GitLab, Azure DevOps, and Bitbucket. Our system effortlessly adapts to your environment.

For software architects & developers
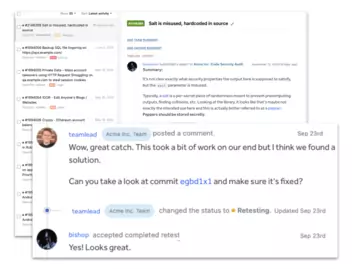
Our findings are contextually delivered inline with your tools for optimal context and collaboration.

For executives & auditors
Wondering what a final Code Security Audit report looks like?
Supporting all programming languages, frameworks, libraries & platforms

Built for your use case
Automated scans catch issues at high volume. Human experts catch the complex.
Code Security Audit harnesses both.
- Network of world-class software engineers
- Comprehensive code review
- One platform—everything you need to eliminate unknown risk
- No code base too large, outdated, or specialized
- Simple integration with source control providers
- Context-specific remediation guidance written by developers for developers
Speak with a security expert
How Code Security Audit works

Get the Code Security Audit Solution Brief
Your quick-reference overview of SDLC defense.
What our customers are saying
Great organization that provides a quality, reliable service to our business.

Audit the Security Posture of DevOps with HackerOne Code Security Audit
.png370a.webp?itok=HXpxbf8p)
How to Catch Injection Security Vulnerabilities in Code Review